 Main Menu
Main Menu |
 Most Favorited Images
Most Favorited Images |
 Recently Uploaded Images
Recently Uploaded Images |
 Most Liked Images
Most Liked Images |
 Top Reviewers
Top Reviewers |
| cockalatte |
650 |
| MoneyManMatt |
490 |
| Jon Bon |
400 |
| Still Looking |
399 |
| samcruz |
399 |
| Harley Diablo |
377 |
| honest_abe |
362 |
| DFW_Ladies_Man |
313 |
| Chung Tran |
288 |
| lupegarland |
287 |
| nicemusic |
285 |
| Starscream66 |
282 |
| You&Me |
281 |
| George Spelvin |
270 |
| sharkman29 |
256 |
|
 Top Posters
Top Posters |
| DallasRain | 70831 | | biomed1 | 63764 | | Yssup Rider | 61304 | | gman44 | 53377 | | LexusLover | 51038 | | offshoredrilling | 48840 | | WTF | 48267 | | pyramider | 46370 | | bambino | 43221 | | The_Waco_Kid | 37431 | | CryptKicker | 37231 | | Mokoa | 36497 | | Chung Tran | 36100 | | Still Looking | 35944 | | Mojojo | 33117 |
|
|
 06-18-2014, 02:38 PM
06-18-2014, 02:38 PM
|
#1
|
|
Gaining Momentum
Join Date: Jul 27, 2013
Location: DFW
Posts: 47
|
 Why no https?
Why no https?
Due to the nature of this site, personal and technical security are of the utmost priority. Given what we found out with the Snowden releases, is that the government IS reading traffic to webistes. So it shocks me to find that ECCIE has not enabled SSL everywhere. What this means for you non techies out there, is that anyone with a network sniffer between your browser and ECCIE's servers can see exactly what you are posting, as it is not encrypted. If ECCIE decides to turn on SSL, then all of that traffic is encrypted.
Givent he costs of SSL certs are so low, my basic question is WHY isn't ECCIE using it by default? Everyone one of our identities, conversations, etc are at risk.
|

|
Quote
 | 1 user liked this post |
 06-18-2014, 03:24 PM
06-18-2014, 03:24 PM
|
#2
|
|
Valued Poster
Join Date: Apr 21, 2014
Location: Austin, TX
Posts: 1,306
|
Probably for the same reason they don't have a robots.txt file.
|

|
Quote
 | 1 user liked this post |
 06-18-2014, 04:38 PM
06-18-2014, 04:38 PM
|
#3
|
|
Valued Poster
Join Date: Dec 24, 2010
Location: .
Posts: 9,776
|
Anyone can see what you are writing on here anyway.
It's a public forum.
Set up Privoxy or hamachi if you wear tinfoil
|

|
Quote
 | 1 user liked this post |
 06-18-2014, 10:13 PM
06-18-2014, 10:13 PM
|
#4
|
|
Valued Poster
Join Date: Apr 30, 2010
Location: second star to the right, and straight on till morning
Posts: 570
|
Better yet, use TOR.
|

|
Quote
 | 1 user liked this post |
 06-22-2014, 09:49 AM
06-22-2014, 09:49 AM
|
#5
|
|
Gaining Momentum
Join Date: May 27, 2014
Location: USA and/or Philippines
Posts: 53
|
You could also use a VPN connection to another part of the USA, so it appears your traffic is located in another area. Your traffic from your PC to the VPN server would be unreadable...
Cyberghost's free option works fairly well for most things.
|

|
Quote
 | 1 user liked this post |
 07-05-2014, 04:49 PM
07-05-2014, 04:49 PM
|
#6
|
|
Thank God it's Firday!
Join Date: Dec 12, 2009
Location: Austin, TX
Posts: 2,698
|
Quote:
Originally Posted by Gotyour6

Anyone can see what you are writing on here anyway.
It's a public forum.
Set up Privoxy or hamachi if you wear tinfoil
|
Without https, snoops can see your passwords, and any PM's you send. They can also see which posts you read. They can also see your IP address.
In this case, "snoops" includes
- Anyone within WiFi range if you're on a public hotspot, including hotels.
- Your ISP
- Anyone with access (legal or illegal) to the network at any one of the links in the internet between you and the website you're going to.
- Anyone with a bogus WiFi hotspot you connect to. These are getting common at places like restaurants, airports, etc.
|

|
Quote
 | 2 users liked this post |
 07-07-2014, 06:07 AM
07-07-2014, 06:07 AM
|
#7
|
|
Valued Poster
Join Date: Aug 5, 2010
Location: World Citizen
Posts: 886
|
@ the OP- things are only at risk if you allow your Tech/Comm security to be lax.
What can anyone prove using information from a Fantasy site, with people using fake names, and writing fiction? Nothing! Now if your Security is lax, it may lead to other problems, but that is on you the Hobbiest.
HTTPS is absolutely justified and required in certain internet scenarios and transactions, but this does not have to be one of them.
Be more concerned with one's own local vulnerabilities on their own computer.
|

|
Quote
 | 1 user liked this post |
 12-23-2015, 07:10 PM
12-23-2015, 07:10 PM
|
#8
|
|
Registered Member
Join Date: Dec 24, 2013
Location: USA
Posts: 13
|
 HTTPS really should be the default everywhere...
HTTPS really should be the default everywhere...
The general thinking is that https should be the default everywhere, since people leak clues about themselves in lots of not-including-credit-card-number web activity that puts them at risk from criminals, et alia. All websites should really be using TLS all the time, especially considering the overhead isn't all that high and certificates can range from inexpensive to free (the latter in fairly restrictive cases, but still).
All sites using user/password credential SHOULD use HTTPS, period.
Using VPN or whatever alone isn't enough, security benefits enormously from having layers, since every layer tends to be somewhat permeable.
jframe2, you are seriously on the wrong end of things at the moment, since every one of your four sentences is essentially wrong.
* Things are always at risk, even if your security is robust
* Lots of things can be inferred about people from what people write, even if the idea is that security doesn't matter, which obviously isn't correct on Eccie.
* HTTPS is absolutely justified in almost all cases, there are few circumstances where it isn't, and Eccie isn't one of them.
* HTTPS protect against vulnerabilities of a certain class on the network, which has nothing to do with your own computer, and which isn't fully addressed by VPNs.
|

|
Quote
 | 4 users liked this post |
 08-21-2016, 07:06 PM
08-21-2016, 07:06 PM
|
#9
|
|
Registered Member
Join Date: Aug 13, 2016
Location: DFW
Posts: 6
|

Quote:
Originally Posted by ravishme

The general thinking is that https should be the default everywhere, since people leak clues about themselves in lots of not-including-credit-card-number web activity that puts them at risk from criminals, et alia. All websites should really be using TLS all the time, especially considering the overhead isn't all that high and certificates can range from inexpensive to free (the latter in fairly restrictive cases, but still).
All sites using user/password credential SHOULD use HTTPS, period.
Using VPN or whatever alone isn't enough, security benefits enormously from having layers, since every layer tends to be somewhat permeable.
jframe2, you are seriously on the wrong end of things at the moment, since every one of your four sentences is essentially wrong.
* Things are always at risk, even if your security is robust
* Lots of things can be inferred about people from what people write, even if the idea is that security doesn't matter, which obviously isn't correct on Eccie.
* HTTPS is absolutely justified in almost all cases, there are few circumstances where it isn't, and Eccie isn't one of them.
* HTTPS protect against vulnerabilities of a certain class on the network, which has nothing to do with your own computer, and which isn't fully addressed by VPNs.
|
Right on. The login function alone warrants using HTTPS. I wish a site admin would chime in on this.
|

|
Quote
 | 1 user liked this post |
 08-21-2016, 09:49 PM
08-21-2016, 09:49 PM
|
#10
|
|
Valued Poster
Join Date: Nov 8, 2013
Location: okc
Posts: 1,264
|
Quote:
Originally Posted by Gotyour6

Anyone can see what you are writing on here anyway.
It's a public forum.
Set up Privoxy or hamachi if you wear tinfoil
|
Https at sign in but Http for the rest of the site
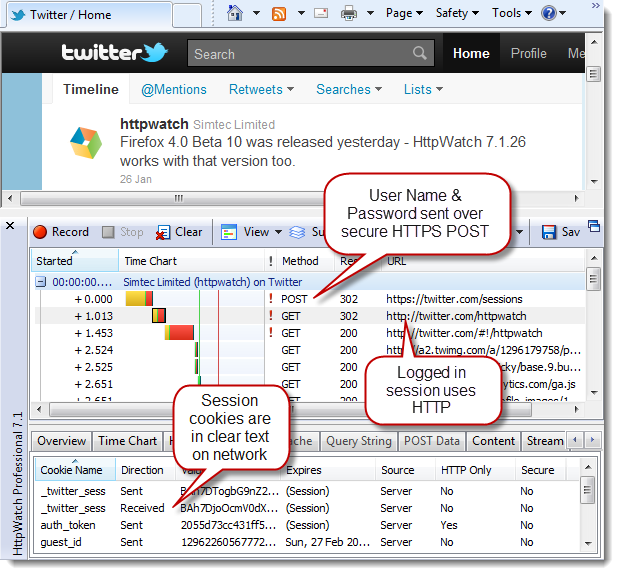
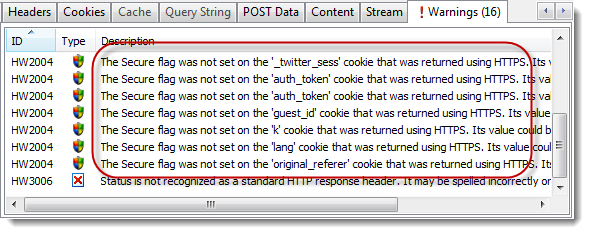
|

|
Quote
 | 1 user liked this post |
 11-28-2016, 03:01 AM
11-28-2016, 03:01 AM
|
#11
|
|
Registered Member
Join Date: Apr 26, 2012
Location: Texas
Posts: 3
|
Quote:
Originally Posted by guynmotion

Right on. The login function alone warrants using HTTPS. I wish a site admin would chime in on this.
|
It's really beyond irresponsible at this point to not require this sensitive server to require a TLS connection. I mean the technology is only ~18 years old now, and it amounts to flipping a bit in most server applications. Why is this not being done? Are they looking for a competitor to fill this trivially-remedied security void?
|

|
Quote
 | 1 user liked this post |
|
 AMPReviews.net
AMPReviews.net |
 Find Ladies
Find Ladies |
 Hot Women
Hot Women |
|
